SQL-injectie 101: Wat is SQLi en hoe aanvallen te voorkomen
06 augustus 2022 - beveiliging
Wat is SQL-injectie
SQL-injectie (SQLi) is een type aanval waarmee criminelen kwaadaardige SQL-statements kunnen uitvoeren op kwetsbare webapplicaties. Aanvallers kunnen toegang krijgen tot gevoelige gegevens, zoals klantgegevens, persoonlijke gegevens, bedrijfsgeheimen en meer door de beveiligingsmaatregelen van applicaties te omzeilen. Hier bespreken we SQL-injectie, hoe het werkt en hoe u aanvallen kunt voorkomen.
SQL-injectieaanvallen kunnen plaatsvinden op elke website die een SQL-database gebruikt. Dit type aanval geeft aanvallers toegang tot essentiële gegevens. Ze kunnen consumenteninformatie, persoonlijke gegevens, handelsgeheimen en intellectueel eigendom inzien. Volgens OWASP is dit een van de ernstigste soorten aanvallen op webapplicaties.
Soorten SQL-injectie
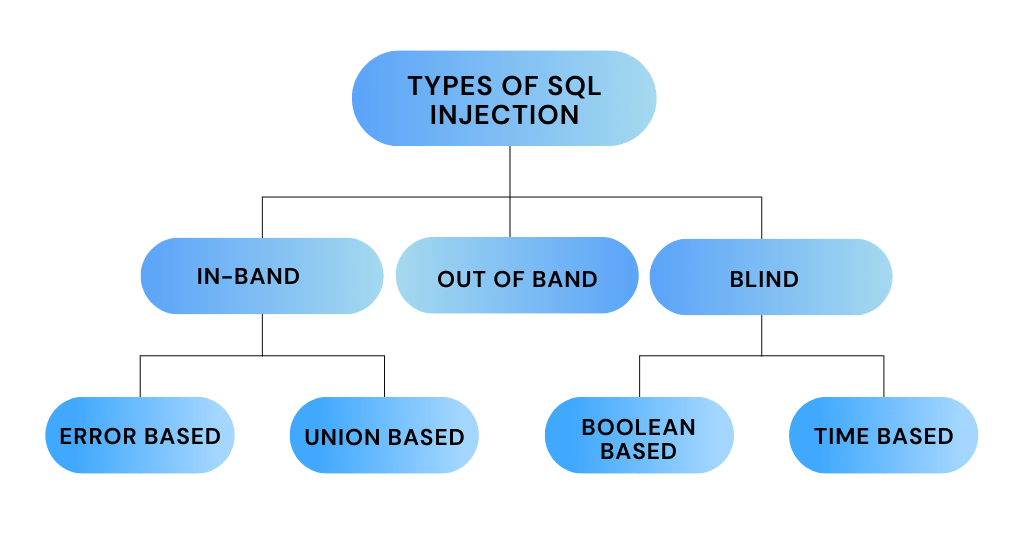
In-band SQLi
In-band SQL-injectie is een aanval waarbij de aanvaller hetzelfde kanaal gebruikt om query's te verzenden en te ontvangen. In-band betekent dat het antwoord wordt verkregen via hetzelfde communicatiemedium. Het doel van de aanvaller is om het antwoord onmiddellijk in een webbrowser te krijgen, indien mogelijk wanneer de aanval handmatig met een webbrowser wordt uitgevoerd.
Voorbeeld van SQL-injectie in de band
De meest voorkomende manier voor een aanvaller om een in-band SQL-injectie uit te voeren is door het verzoek te wijzigen zodat ze de persoonlijke gegevens van de huidige gebruiker kunnen zien. Dit kan worden gedaan door de waarde te veranderen die als onderdeel van het verzoek wordt verzonden. Als de verklaring bijvoorbeeld de naam van de gebruiker zou moeten weergeven, kan de aanvaller deze wijzigen zodat in plaats daarvan zijn naam wordt weergegeven.
SELECT * FROM users WHERE user_id LIKE 'current_user'.
Op fouten gebaseerde SQLi en op unies gebaseerde SQLi zijn de twee meest voorkomende vormen van in-band SQL-injectie.
Op fouten gebaseerde SQLi
Een op fouten gebaseerde SQLi-techniek is een in-band SQL-injectiebenadering die gebruikmaakt van foutmeldingen van de databaseserver om de architectuur van de database te ontdekken. Op fouten gebaseerde SQL-injectie is de meest voorkomende vorm van in-band SQL-injectie.
Voorbeeld van op fouten gebaseerde SQLi:
Als een aanvaller probeert in te loggen met de volgende gegevens:
gebruikersnaam: ' OR 'a'='apwachtwoord: iets
De database zal een fout teruggeven omdat het statement syntactisch onjuist is. De foutmelding onthult informatie over de database, die de aanvaller in zijn voordeel kan gebruiken.
SQLi op basis van unies:
In-band SQL-injectie is een manier om informatie van een website te halen met behulp van de UNION operator om de uitvoer van twee of meer SELECT statements te combineren.
Blinde SQL-injectie
Blinde SQL-injectie is een aanval waarbij de aanvaller antwoorden uit de database probeert te krijgen door vragen te stellen die resulteren in een waar of onwaar antwoord. De aanvaller gebruikt foutmeldingen om te zien of de applicatie anders reageert wanneer een specifieke code wordt gebruikt.
Als een hacker SQL-injectie gebruikt, kan de webtoepassing kritieke databasewaarschuwingen weergeven waarin staat dat de SQL-query onjuist is. Blinde SQL-injectie werkt op dezelfde manier als traditionele SQL-injectie, met uitzondering van de manier waarop gegevens uit de database worden verkregen. Als een database niet genoeg informatie bevat voor een aanvaller om te exploiteren, moet een aanvaller een reeks vragen stellen om gegevens te verkrijgen.
Blinde SQL-injectie wordt onderverdeeld in blinde-booleaanse SQL-injectie en blinde-tijd SQL-injectie.
Booleaans-gebaseerde blinde SQLi
Booleaanse Blinde SQL-injectie is een aanval waarbij de aanvaller antwoorden uit de database probeert te krijgen door vragen te stellen die resulteren in een waar of onwaar antwoord. De aanvaller gebruikt foutmeldingen om te zien of de applicatie anders reageert wanneer een specifieke code wordt gebruikt.
Voorbeeld van booleaans gebaseerde blinde SQLi:
Als een aanvaller het databasetype wil achterhalen, zal hij de volgende verklaring gebruiken:
SELECT * FROM users WHERE user_id LIKE 'current_user' en database() like '%type%'.
Als de database MySQL is, ziet de uitvoer er ongeveer zo uit:
U hebt een fout in uw SQL-syntax; controleer de handleiding die bij uw MySQL-serverversie hoort voor de juiste syntaxis die u moet gebruiken bij 'en database() als '%type%" op regel
Op tijd gebaseerde blinde SQL-injectie
Bij een tijdgebaseerde Blind-aanval wordt een SQL-commando naar de server gestuurd met code die ervoor zorgt dat query's langzamer worden uitgevoerd.
Met tijdgebaseerde blinde aanvallen kunnen aanvallers gegevens extraheren op basis van toegangstijd. Zo'n aanval staat bekend als een blinde of inferentiële injectie aanval. Dit is een type aanval waarbij er geen data stroomt tussen de aanvaller en de database, maar omdat er geen respons is, staat het ook bekend als een blinde injectie aanval.
De responstijd geeft aan of het antwoord goed of fout is. Als het antwoord negatief is, zal de indringer een nieuw verzoek doen. Deze aanvalstechniek is traag omdat de hacker elk karakter afzonderlijk moet doorlopen, vooral bij het aanvallen van enorme databases.
Voorbeeld van blinde SQLi
In dit voorbeeld probeert de aanvaller te bepalen of de gebruiker met id=999 bestaat in de database. Hiervoor gebruiken ze het volgende statement:
ALS(SUBSTRING((SELECT wachtwoord FROM gebruikers WHERE gebruiker_id=999),0, LEN('geheim'))='geheim', SLAAP(30), 'onwaar')
Als de gebruiker met id 999 bestaat in de database en zijn wachtwoord is geheim, dan zal de toepassing 30 seconden slapen. De applicatie retourneert false als de gebruiker niet bestaat in de database.
Buiten de band SQLi
Iemand die gegevens wil stelen, kan SQL-code naar een databaseserver sturen op een manier die geen deel uitmaakt van de gebruikelijke communicatie tussen de server en andere computers. Dit kan gedaan worden door informatie naar de server te sturen via DNS of HTTP verzoeken.
De respons van de app wordt niet beïnvloed door het al dan niet terugsturen van gegevens, of er al dan niet een probleem is met de database, of hoe lang het duurt om de query uit te voeren. Out-of-band kan worden gebruikt in netwerkinteracties om gebeurtenissen naar believen af te vuren. Afhankelijk van een geïnjecteerde voorwaarde kunnen deze voorwaardelijk geactiveerd worden om stukje bij beetje kennis te vergaren.
Gegevens kunnen ook uitlekken via verschillende netwerkprotocollen van netwerkinteracties. De afbeelding geeft het verzoek weer dat van de webapplicatie naar de database van de app wordt gestuurd.
Voorbeeld van out-of-band SQLi
In dit voorbeeld probeert de aanvaller te bepalen of een specifieke gebruiker bestaat in de database. Om dit te doen, gebruiken ze de volgende verklaring:
SELECT user_id FROM users WHERE username='$username' AND password='$password' LIMIT 0,0 UNION SELECT NULL,'' INTO OUTFILE '/var/opt/databases/$filename.php'; --
De applicatie geeft hun gebruikers-ID terug als de gebruiker bestaat in de database. Als de gebruiker niet bestaat in de database, dan maakt de applicatie een bestand aan dat PHP-code bevat die kan worden gebruikt om systeemcommando's uit te voeren. De aanvaller kan dit bestand dan gebruiken om commando's op de server uit te voeren.
Hoe een SQL-injectie voorkomen
De beste manier om je te beschermen tegen SQL-injectieaanvallen is het gebruik van invoervalidatie, prepared statements en query's met parameters. De code mag nooit direct gebruik maken van de invoer van de gebruiker. Ontwikkelaars moeten alle invoer zuiveren in plaats van alleen webformulierinvoer zoals aanmeldingsformulieren. Enkele aanhalingstekens moeten worden verwijderd uit alle twijfelachtige codecomponenten. Het is ook een goed idee om databaseproblemen op live sites te verbergen om te voorkomen dat ze onbedoeld worden onthuld. SQL-injectie kan informatie over een databasesysteem opleveren die aanvallers in hun voordeel kunnen gebruiken.
Als u een probleem ontdekt met uw website, moet u deze onmiddellijk offline halen en contact opnemen met uw hostingprovider. Zij kunnen u helpen bepalen of uw site al dan niet is aangetast en welke stappen u moet nemen om het probleem op te lossen. Zorg er in de tussentijd voor dat alle gebruikers van uw website op de hoogte zijn van het probleem en hun wachtwoorden zo snel mogelijk wijzigen.
Preventietips om SQL-injecties te vermijden
Er zijn een paar manieren om SQL injectie kwetsbaarheden in je programmeertaal en database setup te vermijden. Deze technieken kunnen worden gebruikt met de meeste databases, zoals XML. Je kunt deze technieken gebruiken om je databases veiliger te maken.
1) Gebruik van goed opgebouwde opgeslagen procedures
Beginners moeten eerst leren hoe ze verklaringen met variabelen kunnen maken. Dit is eenvoudiger dan het maken van dynamische queries en het is gemakkelijker te begrijpen. Geparameteriseerde queries zijn queries waarbij de ontwikkelaar alle SQL-code maakt en vervolgens elke parameter op een later tijdstip invoert. Met deze methode kan de database onderscheid maken tussen broncode en informatie.
Prepared statements helpen ervoor te zorgen dat het doel van een query niet wordt veranderd, zelfs als iemand SQL-instructies probeert te geven.
2) Validatie invoer toestaan-lijst
SQL-query's gebruiken bindvariabelen op specifieke plaatsen voor gegevens. Als je bijvoorbeeld Python gebruikt, zou je de %s plaatshouder. Je kunt een reguliere expressie gebruiken om gebruikersinvoer te valideren aan de hand van de toegestane lijst voor welke tekens zijn toegestaan in elke bindvariabele.
Als je JavaScript gebruikt, kun je \w om alfanumerieke en underscore tekens te matchen.
De allow-list moet zo specifiek mogelijk zijn om valse positieven te voorkomen.
Als je bijvoorbeeld op zoek bent naar een telefoonnummer in de VS, zou je de volgende reguliere expressie gebruiken:
/^\d{11}$/
Dit zou overeenkomen met een reeks van 11 cijfers die een telefoonnummer zou kunnen zijn. Als iemand iets als 'abcdef', komt het niet overeen en is de invoer ongeldig.
Dit zorgt ervoor dat je gegevens veilig en gezond zijn. Als je waarden uit code moet gebruiken in plaats van gebruikersparameters, dan is dat ook goed!
Stel echter dat parameterwaarden van gebruikers gericht zijn op specifieke tabel- en kolomnamen. In dat geval moeten de parameterwaarden worden toegewezen aan de overeenkomstige tabel- en kolomnamen om ervoor te zorgen dat ongeldige gebruikersinvoer niet in de query terechtkomt.
3) Gebruik witte lijsten
Filter gebruikersinvoer niet op basis van zwarte lijsten met slechte tekens. Het is veel effectiever om toegestane lijsten te gebruiken met goede tekens die in specifieke velden worden verwacht. Dit stopt SQL-injectieaanvallen voordat ze beginnen.
Laat bijvoorbeeld alleen cijfers en streepjes toe in het invoerveld als je een telefoonnummer verwacht. Als je een e-mailadres verwacht, laat dan alleen tekens toe die geldig zijn in een e-mailadres.
4) Gebruik de meest actuele platforms
PHP heeft geen SQLi-beveiliging in oudere platforms voor webontwikkeling. Gebruik de meest recente versie van de beschikbare programmeeromgeving, taal en bijbehorende technologieën. Gebruik in dit voorbeeld liever PDO in plaats van PHP.
5) Scan uw webapplicatie regelmatig
SQL-injecties kunnen erg moeilijk te vinden zijn. Het is belangrijk om je webapplicatie regelmatig te scannen op kwetsbaarheden.
6) Minst bevoorrechte positie afdwingen
Het principe van de laagste privileges is een beveiligingsconcept dat gebruikers beperkt tot de minimale hoeveelheid toegang die ze nodig hebben om hun werk te doen. Dit omvat het beperken van het aantal accounts dat gebruikers hebben en de privileges die deze accounts hebben.
Least Restriction on Functionality (LRF) is de praktijk en het concept van het beperken van gebruikersrechten, accounts en computerprocessen tot alleen die middelen die nodig zijn voor basale, acceptabele taken. Dit helpt om minimale gebruikersrechten of toestemmingsniveaus te handhaven, wat essentieel is voor mensen om hun werk effectief uit te voeren.
Least privilege is een beveiligingsprincipe dat vereist dat applicaties, systemen en gadgets alleen de rechten hebben die nodig zijn om een specifieke taak uit te voeren. Op deze manier blijft de impact beperkt als iemand er in slaagt om een kwetsbaarheid uit te buiten en schade aan te richten. Dit in tegenstelling tot het geven van meer rechten aan gebruikers dan ze nodig hebben, wat het risico op grote schade bij een SQL aanval vergroot.
SQL-injectie - Veelgestelde vragen
In-band SQL-injectie is de meest voorkomende vorm van SQL-injectieaanval. Het treedt op wanneer een aanvaller hetzelfde communicatiekanaal kan gebruiken om de payload af te leveren en resultaten te verzamelen.
De beste verdediging tegen SQL-injectie is het gebruik van query's met parameters. Dit type query gebruikt plaatshouderwaarden voor parameters, die op een later tijdstip worden ingevuld. Met deze methode kan de database onderscheid maken tussen broncode en informatie.
SQL-injectie kan op verschillende manieren worden gedetecteerd. Eén methode is het gebruik van een web application firewall (WAF). Een WAF is een stuk hardware of software dat zich tussen een webapplicatie en het internet bevindt. Het inspecteert verkeer op kwaadaardige activiteiten en kan SQL-injectieaanvallen blokkeren.
SQL-injectie van de tweede orde treedt op wanneer een aanvaller een payload kan injecteren die door de webtoepassing wordt opgeslagen en later wordt uitgevoerd. Dit type aanval is moeilijker uit te voeren omdat de aanvaller een manier moet hebben om de uitvoering van de opgeslagen payload te triggeren.
Blinde SQL-injectie is een aanval waarbij de aanvaller niet direct de resultaten van zijn payload te zien krijgt. In plaats daarvan moeten ze waar of onwaar statements gebruiken om informatie uit de database af te leiden. Dit type aanval is moeilijker uit te voeren, maar kan net zo gevaarlijk zijn als andere typen SQL-injectie.
Een stacked query is een type SQL-injectie waarbij de aanvaller meerdere query's gebruikt om informatie uit de database te halen. Dit type aanval is moeilijker uit te voeren, maar kan erg gevaarlijk zijn als het lukt.
Op fouten gebaseerde SQL-injectie is een aanval waarbij de aanvaller databasefouten gebruikt om informatie uit de database af te leiden. Deze aanval is moeilijker uit te voeren, maar kan zeer gevaarlijk zijn als hij slaagt.

beveiliging
admin is senior staff writer voor Government Technology. Ze schreef eerder voor PYMNTS en The Bay State Banner en heeft een B.A. in creatief schrijven van Carnegie Mellon. Ze woont buiten Boston.