APT (Advanced Persistent Threat)
August 21, 2022 • César Daniel Barreto

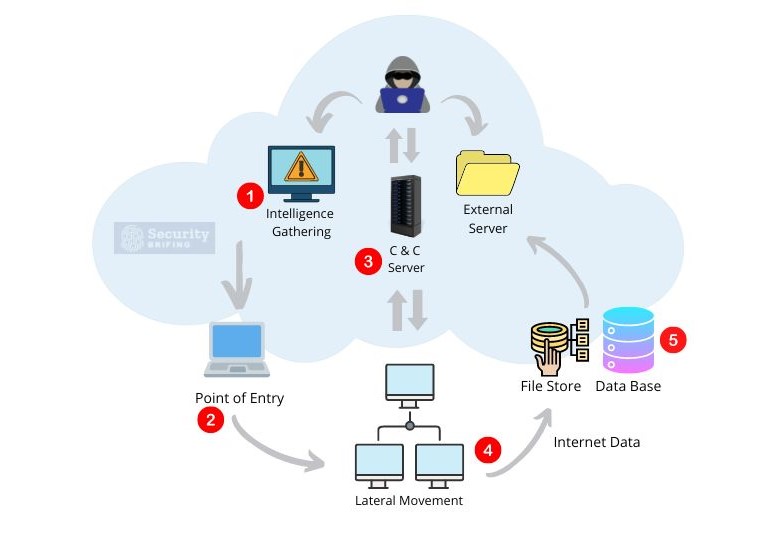
An APT attack is a type of cyberattack carried out by a motivated and well-resourced attacker, who aims to gain long-term access to a target’s network. The attack is carried out in several stages:
- Intelligence Gathering: The APT attacker collects information about the target network, often through phishing emails, malware attachments, and software vulnerabilities.
- Point of Entry: The attacker finds a way into the system to install malware, using techniques such as phishing emails or exploiting software vulnerabilities.
- Command and Control Server: The attacker sets up a communication channel with the malware, usually through an IP address located in another country.
- Lateral Movement: The attacker gains access to multiple machines on the network by exploiting software vulnerabilities and using stolen credentials.
- Data Transfer: The attacker steals data by exfiltrating it, usually compressing and encrypting it to avoid detection.
- Cover-Up: The attacker hides their tracks, deleting files, disabling logging, or using other means to make the attack hard to detect.
How to execute adequate security against the advanced threats
We’ve come to a turning point in security when organizations must accept that they will be hacked. It’s also fair to suppose that any critical systems linked to a network and then exposed to the Internet have already been compromised.
There are no assurances that any organization is free from the threat. It’s suitable for an organization to hope they won’t be hacked, but it makes sense to have detection precautions in place just in case. And when a breach occurs, it can be detected as soon as possible.
It is crucial to find the problem quickly so it does not happen again.
Our top priority is to keep our company floating, and the best way to do that is by detecting data breaches early on and reacting quickly to minimize the damage. Unfortunately, recent events have shown that companies need to do more to see these compromises.
Understanding the risks
Businesses should maintain the same level of caution regarding security as we do in our everyday lives. Would you eat a candy bar off the ground that someone else had already taken a bite of? Of course not! In the same way, businesses shouldn’t take unnecessary risks where they don’t know what could happen or how things could end up.
Unfortunately, when it comes to cyber security, those same common sense concepts have yet to be instilled. It is just as risky to pick up and use a USB stick dropped on the ground as eating food off the floor. However, most people have yet to be taught not to do the latter since childhood. And it is essential to educate people about the dangers in the digital world.
Focus on the organization’s vulnerabilities
We naturally focus on those threats that have the best chance of being exploited and inflicting a significant impact. Ten major vulnerabilities are more accessible to fix than 100 minor ones. Instead of improving one exposure at a time until it’s gone, many organizations make this mistake and hyperfocus on repairing one until it’s fixed rather than reducing many risks simultaneously.
This myopic vision creates a false sense of security and gives CISOs the impression that they’re doing their jobs when, in reality, they’re only making marginal improvements.
Additionally, when an organization’s security is breached, it’s not just the CISO’s job on the line. The whole company’s reputation is at stake. So, everyone in the organization needs to be up-to-date on the latest security threats.
And finally, even if a company has cyber security insurance, more is needed. The average data breach cost is $3.86 million, and that’s just the average! The total cost could be much higher depending on the size of the company and the type of data stolen.
Cybersecurity insurance only covers a fraction of the total cost and doesn’t contribute to improving the company’s security posture. So, even if a company has insurance, it’s still in its best interest to do everything it can to prevent a breach from happening in the first place.
Reduce attack surface
One of the critical areas of preventing APT threats is reducing the attack surface or removing extraneous components that are not being used. Reasonable hardening procedures and solid configuration management is the key to success.
Open ports and scripts can make an organization vulnerable to security breaches. If these services are hacked, the consequences might be disastrous. However, if an organization is using services not for legitimate purposes and those services are compromised, you have every right to be concerned.
Many successful APT assaults have taken advantage of enabled capabilities but are not used for practical purposes.
Organizations can improve their security by reducing the number of software, applications, and systems features. Fewer features mean fewer opportunities for attackers to find a way in.
Be aware of HTML-embedded email content
Organizations that use HTML-embedded content in their email are more susceptible to spear phishing attacks from APTs. While some people use the HTML features in an email to play with colours and backgrounds or embed content, most businesses don’t require HTML for their day-to-day operations.
Sometimes people send you emails with links in them. People might click on the link, thinking it will take them where they want to go. But cybercriminals have found a way to hide the actual destination in the code of the email.
If organizations turned off HTML email, they would stop many spear phishing attacks.
Raise awareness of users
Many dangers enter a network by fraudulent means, such as enticing the user to open an attachment or click a link they should not. Sessions may go a long way toward lowering overall exposure by restricting the actions a user is allowed to perform with appropriate awareness.
Conduct behavior ranking
Often, sophisticated attackers use standard tactics to determine whether something is secure. Even though this method isn’t very reliable, it’s still widely used by innumerable assailants.
Attackers want to go undetected, so you must be careful about their actions. Many attackers try to look like regular traffic. They do this so they can get past security without being noticed. But once they’re inside, they show their true intentions. So you need to watch out for certain types of behavior and figure out if it looks more like a regular user or someone with evil motives.
Create a sandboxing environment
A sandbox is an isolated testing environment that enables users to run programs or execute files without affecting the rest of the system.
A typical business environment has many users who need access to different applications and data. However, not all users require access to all applications and data. Most users only need access to a small subset of the applications and data.
By creating a sandbox environment, businesses can limit the amount of data and applications users can access. A sandbox will minimize the chances of a data breach and reduce the impact if a breach does occur.
In addition, sandboxing can also help to prevent malware from spreading. If a user opens a file containing malware, the malware will be isolated in the sandbox and cannot infect the rest of the system.
Implement least privilege
The least privilege is a security principle that states that users should only be given the minimum level of access necessary to perform their job.
For example, users should only be given editing access if they read data from a database. By restricting users to the minimum necessary access level, businesses can reduce the chances of a data breach.
In addition, businesses should also consider implementing the least privilege for applications. If an application only needs to read data from a database, you should not give it write access. By restricting applications to the minimum necessary access level, businesses can further reduce the chances of a data breach.
Secure the network’s outbound traffic
Since outbound traffic is more likely to contain data stolen from a network, monitoring it is even more critical. By looking at outbound traffic, you can identify any unusual activity and take steps to prevent your company from being harmed.
Understand how the offence operates
To protect your organization from APT attacks, you must understand how the attacks work. You must also stay up-to-date on the latest attack methods to prepare your defences.
Control the endpoint
Attackers may use an endpoint to get into a network, but their main goal is usually to steal data. If you want to protect your data and minimize the impact of an attack, focus on securing and monitoring the endpoint.
Organizations can use many different techniques to control the endpoint. One standard method is to require two-factor authentication (TFA) for all users. TFA ensures that only authorized users can access the data.
Another method is to use application whitelisting. This technique allows only approved applications to run on an endpoint. By controlling what applications are allowed to run, you can reduce the risk of an attack.
You can also use monitoring tools to control the endpoint. These tools can help you detect and respond to suspicious activity.
Implement a data classification system
You must have a suitable data classification procedure to protect your company from APTs. A data classification system means knowing which information is sensitive enough to require protection. One of the problems with APTs is that they constantly try to steal data from your organization. You can only stop some things from leaving your company, but having a suitable data classification procedure will help you defend yourself against these attacks.
The best way to store your data is on an Internet-based storage network. This storage network is very secure and will help keep your data safe. It is also important to only allow necessary information to leave the company so that sensitive data stays intact.
If you have two files, one public knowledge and the other confidential, the confidential file is at a greater risk because people might not know it is secret. An organization can now regulate and manage the flow of information with a data loss prevention (DLP) solution that is closely linked with digital rights management (DRM).
There are several steps in a suitable data classification procedure:
1. Determinate the administrator
2. Specify the types of data
3. Categorize the data
4. Set security controls
5. Train employees on the procedure
6. Monitor and review the procedure
3. Determine the value of the data
4. Classify the data
5. Create a policy
6. Train employees
7. Enforce the policy
8. Monitor compliance
A data classification procedure is an essential part of any security plan. By implementing a classification procedure, you can help protect your company from APTs.
Cyber security is crucial. Organizations will keep getting hacked, but we still fight.
We can’t always stop every attack, but by being prepared and diligent, we can limit the damage that hackers can do.

César Daniel Barreto
César Daniel Barreto is an esteemed cybersecurity writer and expert, known for his in-depth knowledge and ability to simplify complex cyber security topics. With extensive experience in network security and data protection, he regularly contributes insightful articles and analysis on the latest cybersecurity trends, educating both professionals and the public.