Types of known cyberattacks in detail until 2023
April 07, 2023 • César Daniel Barreto

To successfully defend against cyberattacks and risks, it is crucial to comprehend their characteristics and actions. The main categories of cyberattacks are SQL Injection Attacks, Cross-Site Scripting, and Denial of Service (DoS). In this article, we will explore these significant cybersecurity issues.
SQL Injection Attacks
SQL enables communication with data stored in databases, whether they are locally stored or hosted on remote web servers. This language allows us to extract and modify information using scripts or small programs. Many servers storing information for services or applications rely on SQL.
As OPSWAT explains, a SQL injection attack targets these servers, using malicious code to extract stored data. This situation can become particularly concerning if the stored data includes private customer information, such as credit card numbers, usernames, passwords, or classified information.
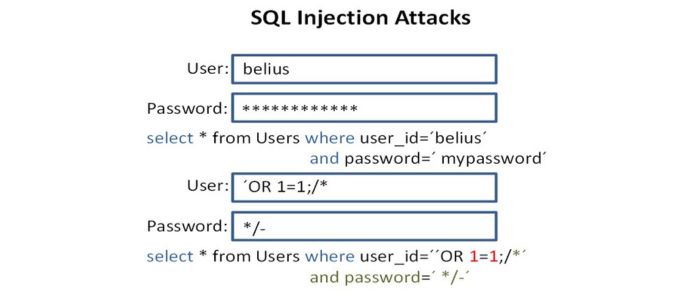
Some prevalent SQL injection examples consist of:
- Accessing concealed data involves altering a SQL query to yield extra results.
- Disrupting application logic by modifying a query to interfere with the application’s intended function.
- UNION attacks, enabling data retrieval from various database tables.
- Investigating the database to gather details about its version and organization.
- Blind SQL injection, where controlled query results are not displayed in the application’s responses.
Cross-Site Scripting (XSS)
In this kind of cyberattack, the user is targeted rather than the server, as the attack is executed in the user’s browser when they access it, not on the server itself. One method for such cross-site attacks is injecting malicious code in a comment or script that runs automatically. Cross-site scripting attacks can severely damage a website’s reputation by compromising user information without leaving any trace or indication of malicious activity.
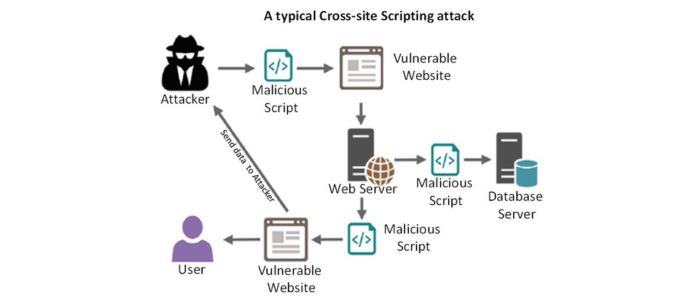
Cross-site scripting (XSS) is a form of cyberattack where malicious individuals inject a harmful script into a website, which is then processed and executed. This attack typically relies on the website’s trust in user input data and involves sending a URL containing the malicious payload to the target user. The primary goal of XSS attacks is to steal personal data, session cookies, and employ social engineering techniques, among other objectives. There are three main types of XSS attacks, and we will now discuss each type and the steps necessary to protect ourselves from them:
- Reflected Cross-Site Scripting: A reflected XSS attack typically injects the payload into an HTTP request parameter. The web application later processes and deploys without validation or escaping. This is the simplest form of XSS, and the malicious script intended to affect the victim’s browser can be easily modified, potentially without the user detecting the attack.
- Stored Cross-Site Scripting: In this variant, the web application stores the input value, which includes the harmful script, in a storage medium. The script persists until the application retrieves the value and incorporates it into the HTML document. Common entry points for this vulnerability include website comments, blog posts, usernames, chats, contact forms, and order details. Persistent XSS can come from various sources, with HTTP protocol responses being the most common and messages through SMTP, instant messaging services, and socket notifications.
- DOM-based Cross-Site Scripting: The Document Object Model (DOM) is a programming interface that represents a web document’s structure and connects it to a scripting language. It allows for the organization of documents like HTML or XML and enables programs to alter the document’s structure, style, and content. In a DOM-based XSS attack, the malicious payload is executed by modifying the DOM environment in the victim’s browser, leading the user to unknowingly run client-side code. With the rise of JavaScript libraries, processing data from untrustworthy sources (insecure or improperly encoded) on the client side has become increasingly common, often writing this data to the website’s DOM.
The Evolution of Cross-Site Scripting (XSS)
Since the initial discovery of the vulnerability, extensive research has been carried out in this domain. As programming languages progress, new methods to exploit Cross-Site Scripting arise, due to the diverse range of programming languages and web development approaches. An intriguing example is JSFuck, a programming style utilizing only six characters that can generate and execute JavaScript code with minimal characters, based on the JavaScript language itself. It’s essential to consider this programming style when devising strategies to mitigate any form of Cross-Site Scripting.
Denial of Service (DoS) and Distributed Denial of Service (DDoS)
These attacks involve flooding a website with traffic, causing its server to become overwhelmed with requests, and rendering it unable to display content to users. In many instances, these cyberattacks are executed by multiple computers concurrently, making them particularly difficult to counter. Attackers can originate from various IP addresses worldwide, further complicating identifying the potential source.
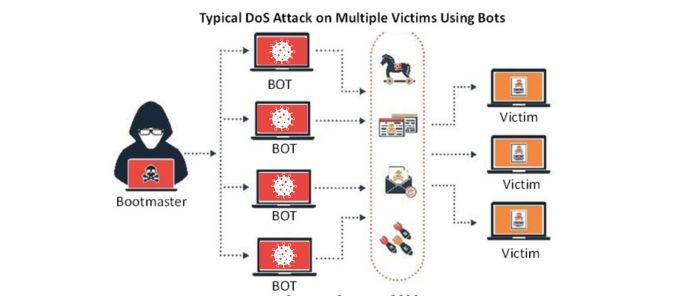
This cyberattack aims to incapacitate a system, application, or machine, obstructing its intended service. The attack may target the information source (e.g., an application), communication channel, or computer network. Web servers have a limited capacity for handling requests or user connections; surpassing this limit can slow down or halt the server’s response, potentially causing disconnections. Denial of service (DoS) and distributed denial of service (DDoS) are two techniques for executing such attacks. The primary distinction is the number of computers or IPs participating in the attack.
In DoS attacks, numerous requests to the service originate from the same machine or IP address, consuming the resources provided. Eventually, the service becomes overwhelmed and begins to reject requests, resulting in a denial of service. DDoS attacks, on the other hand, involve multiple computers or IP addresses simultaneously targeting the same service. DDoS attacks are more challenging to detect because the requests originate from various IPs, making it impossible for administrators to block the requesting IP as they could in DoS attacks.
Computers participating in a DDoS attack are enlisted through malware infection, turning them into bots or zombies that cybercriminals can remotely control. A group of bots, i.e., computers infected with the same malware, forms a botnet known as a zombie network. This network has a significantly higher capacity to overwhelm servers than an attack executed by a single machine.
Conclusion
Thus, based on the aforementioned information, existing cyberthreats include Malware, Ransomware, Viruses, Worms, Trojans, Denial of Service, Rootkits, Phishing, Spyware, Adware, and combinations of these supported by various cyberattack mechanisms.
These attack types often rely on one another, employing multiple techniques within a single attack. For instance, a Trojan might be deployed to initiate a DDoS attack later on, while a Rootkit could be executed after obtaining passwords through phishing.
Cybersecurity experts recommend being wary of free antivirus software, as its installation may lead to unforeseen consequences. It is essential to understand that absolute security does not exist. Individuals will always be dedicated to discovering vulnerabilities in systems and applications to exploit them maliciously. However, achieving a high degree of protection is possible.
César Daniel Barreto
César Daniel Barreto is an esteemed cybersecurity writer and expert, known for his in-depth knowledge and ability to simplify complex cyber security topics. With extensive experience in network security and data protection, he regularly contributes insightful articles and analysis on the latest cybersecurity trends, educating both professionals and the public.