Cybercrime Through WiFi: What You Need to Know
February 25, 2023 • César Daniel Barreto

Cybersecurity is considered a priority by corporations and companies, and they are making significant investments in firewalls that allow their systems to be effectively inaccessible. However, many of these companies are unaware of the exposure to cybercrime generated by their WIFI network.
Faulty WIFI, coupled with insufficient understanding of the obvious signs of cyberthreats, can inadvertently give cybercriminals access to sensitive insider business information. In addition, it can also expose employees to the disastrous risk of identity theft, phishing, and other cyber-scams. What many do not realize is that their WIFI can invalidate their attempts to protect assets. We must be aware that we are exposed to the attack of the “man in the middle” (MITM). However, with the right organizational knowledge and simple technology, it can be easily prevented.
Cyber attack mode through WIFI
Cybercrime does not rest, and cybercriminals are constantly evolving, targeting organizations and focusing their attention on individual users. In the digital world, where connectivity and wireless access are a necessity, online opportunists seek to take advantage.
Rogue access points
Cybercriminals intercept data running through wireless access points and use that data for criminal gain. The procedure uses inexpensive technology that allows cybercriminals to set up “fake” access points or rogue networks that masquerade as legitimate WIFI access points with a familiar title. They then observe keystrokes and illegally take personal data, and in most cases confidential information, from anyone who joins the network. Since these rogue access points are not encrypted, all activity that runs through them is completely open and visible to anyone willing to look for it.
Interception of data
Interception of data such as passwords and usernames can allow illegal access to sensitive information, including online banking, credit card information, and corporate permits. A cybercriminal may not use the information right away, but they can breach these accounts, and the information contained in them, at any time.
Lateral movement
The concern for most users stems from the private and sometimes confidential documentation they keep on their devices, but cybercriminals are rarely interested in this type of documentation. They are more interested in the lateral movement of an unwitting victim’s email account. For example, if a hacker has access to your email account, it gives them the ability to turn on password notifications from sites like PayPal and monitor keystrokes as you enable new login details.
Public vs. corporate WIFI
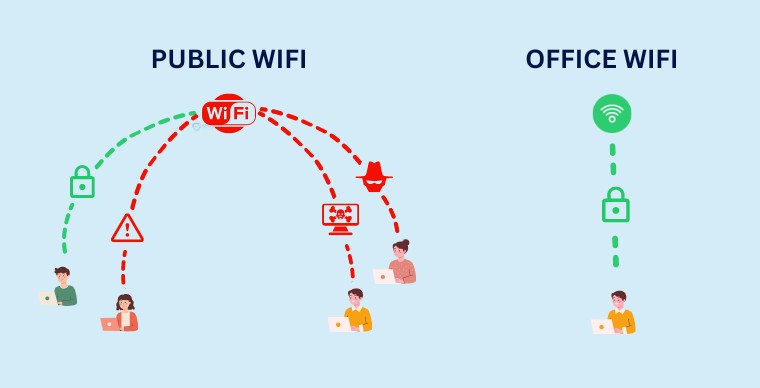
WIFI spying cases around the world are on the rise. Cybercriminals have caught many high-profile victims, hacking into the wireless networks of household brands like Starbucks, American Airlines, and TalkTalk. The move has even prompted the FBI to alert users to access their environment before joining a network.
False sense of security
This has increased the misconception that eavesdropping is limited to public WIFI only, adding to the false sense of security that office-based networks are not resistant to attack, and this is incorrect. A WIFI network is just as likely to be compromised in an office environment as it is in a shopping mall, hotel lobby, or even an airport.
Cybercriminal tactics
A cybercriminal with the right technology could be sitting on the other side of the wall, in the parking lot outside the office, or even in the building next door. They certainly don’t differentiate between a public or corporate WIFI network. Their goal is simply to lure unsuspecting users into their networks and rogue access points and launch their cyber attacks from there.
How can we protect ourselves?
Despite the increase in WIFI cyberattacks, only a small number of companies have implemented the correct training and procedures to address the threat of WIFI eaves
dropping. Many even believe that password encryption alone offers a sufficient defense, but unfortunately, this is not the case. Encryption is only applicable when a user consciously chooses a legitimate network. If you select a rogue access point, the wireless key that protects your network is not needed in the first place.
Organizations are legally responsible for the traffic and information that passes through their network. Employees have a duty to care for their employees and should do everything in their power to ensure that their networks are secure. However, given the obstacles, how can they reduce the risk of MITM attacks? A multi-layered technique is needed that merges technology and education.
Points to consider
More emphasis should be placed on ensuring that users understand the hazards and can perceive any abnormal behavior. While cybercriminals are becoming increasingly sophisticated, their method often follows familiar patterns that, if people are vigilant, possibly raise the alarm. Here are some points to consider:
- Know your company’s WIFI: Joining a strange hotspot often requires unconventional behavior. Cybercriminals will usually reroute you to a malicious and unsafe website that imitates a legitimate login page. All these pages are not encrypted, so if you log in, all your transactions and data become visible. So get familiar with your company’s WIFI SOPs; know what is going on and stop immediately if something seems strange. If you’re being redirected to a portal, particularly in a work environment, that’s usually a red flag.
- Look for the lock: If you are working remotely and join public WIFI, it is not uncommon to get redirected to a portal, and most are not malevolent. You can look for a lock icon in the address bar, as this is usually the sign of a legitimate site.
- Know your network: Your device will continually search for recognizable WIFI networks that it has previously joined. Cybercriminals will imitate them, setting up rogue access points with the same title, in the hope that you’ll connect automatically, so be vigilant. If you are browsing the web at McDonald’s and are asked to join their corporate WIFI, it is most likely a scam.
Increasing cybersecurity in the WIFI network
Technology can offer protection against MITM attacks. Rogue access point detection tools can help to recognize, delimit, and remove rogue access points. Running from legitimate access points, these types of solutions record and inspect activity traveling through your WIFI network and can flag any suspicious behavior as they provide visibility and security.
Also, some companies have launched policies to ensure that customer devices and machines can only connect to certain WIFI or trusted networks, eradicating the risk of unauthorized WIFI. The most proactive have also turned to certificate-based authentication to ensure users that their security is constantly protected. Good examples of this can be seen on your local high street, where retailers assure customers that they are ‘WiFi Friendly’ certified. It is an example that corporate organizations should follow.
Best practices to protect yourself
In a world where both mobility and connectivity have become essential for global communication, WIFI is a vital component of the digital workplace, and users now expect it. But they also expect their online communications and data to be safe from the cyber threat of cyberattacks.
Here are some best practices to protect yourself from WIFI cybercrime:
- Stay away from suspicious websites and messages.
- Create strong passwords that are long, complex, and unique.
- Use a password manager from a trusted provider.
- Enable two-factor authentication when possible.
- Never reuse passwords for more than one account or service. If your password is stolen in an attack, the damage is multiplied since they can access different accounts.
- Monitor your bank and credit accounts regularly for suspicious activity. This could help you spot an attack before it does major damage to your finances or reputation. Also, set limits for transactions to prevent misuse of your money.
- Be careful with your confidential information. If you want to get rid of documents that contain sensitive personal information, make sure to do it in a safe way, destroying them so that they are irretrievable. Apply the same common sense to your devices: when you dispose of or sell them, make sure you leave no trace of your sensitive information behind.
- Don’t share too much. Avoid posting details about your personal life, which could be misused by criminals to act on your behalf.
It’s also important to stay up-to-date with the latest cyber threats and trends. Cybercriminals are always evolving, and so should your knowledge of how to protect yourself and your organization. Participating in cybersecurity training programs and staying informed about the latest tactics and technologies can go a long way in preventing attacks.
In conclusion, WIFI networks are a convenient and essential part of modern life, but they also pose significant risks for cybercrime. It’s crucial to be aware of these risks and take steps to protect yourself and your organization. By implementing the right security measures, being vigilant, and educating yourself and others, you can reduce the likelihood of becoming a victim of WIFI cybercrime.
César Daniel Barreto
César Daniel Barreto is an esteemed cybersecurity writer and expert, known for his in-depth knowledge and ability to simplify complex cyber security topics. With extensive experience in network security and data protection, he regularly contributes insightful articles and analysis on the latest cybersecurity trends, educating both professionals and the public.