Introduction to OpenVPN
October 05, 2022 • César Daniel Barreto
The internet is just as important as any other public service in today’s world. The first thing on everyone’s mind when purchasing a new home or opening up a firm in a new location is a reliable internet connection, followed by electricity, heating, garbage collection, and (but not necessarily) a phone service.
Some may claim that the phrase “third-world” is incorrect and insulting. With programs like “One Laptop per Child” and initiatives by firms like Facebook and Google, many so-called third-world nations now have internet access with no running water or sewer systems.
But with the good comes the bad. While anyone can put up a website, create a Facebook account, or open a Twitter handle, not everyone does so with good intentions, hackers and criminals included. When there are many users, there is an increased risk of someone trying to exploit the system for personal gain.
OpenVPN is an open-source project that started in 2002 intending to create a full-featured SSL VPN solution. OpenVPN encrypts data sent across networks, which is especially important when many users are on the same network.
The history of interceptions and how they’ve progressed over time
Historically, you could depend on a message remaining unaltered if it was delivered in a wax-sealed letter by someone trustworthy. However, as time progressed, intercepting correspondence became simpler: The sender was able to read or tamper with it before passing it along.
Technological advances during World War II enabled both sides to protect their data more securely through examples such as the Enigma machine and Navajo code talkers. After the war, the US government used these and other techniques to protect its information.
As time went on and technology evolved, new ways were needed to keep data secure, which is where OpenVPN comes in. OpenVPN uses a combination of public-key cryptography and SSL/TLS for key exchange. OpenVPN can run over User Datagram Protocol (UDP) or Transmission Control Protocol (TCP). OpenVPN offers many features, such as tunnelling IPv4 or IPv6 traffic, running over a single port, and more.
Community Edition & OpenVPN Tunneling Protocol
OpenVPN is available in two versions: OpenVPN Community Edition, which is free and open-source, and OpenVPN Tunneling Protocol, which is a commercial product.
OpenVPN Community Edition
OpenVPN is an open-source project that anyone can contribute to and runs under a GPL license. Setting up CE is free if you’re familiar with Linux and the command line interface.
The OpenVPN Community Edition is available for download on the OpenVPN website.
OpenVPN Tunneling Protocol
The OpenVPN tunneling protocol uses SSL encryption to guarantee that the data is protected. This is because AES-256 encryption is utilized, which is a standard used by the U.S. government. The code for audits is available to everyone. This means that people can find and fix vulnerabilities. In addition, the protocol provides faster connections and can get past most firewalls.
Other benefits of the OpenVPN Tunneling Protocol include:
- Supports: Windows, macOS, Linux, iOS, Android
- Connects: Up to 5 devices at faster speeds with OpenVPN 2.4P
- Tunneling: The OpenVPN tunneling protocol can tunnel through firewalls and NATs
- API: Easy-to-use API for developers
What is a VPN?
An administrator may join a few PCs on different networks to create the illusion that they share the same local network. The machines might be in the same room, on opposite sides of the world, or utilizing various connection types, such as wireless uplinks, satellite, and dial-up connections.
The letter “P” in VPN stands for privacy, so the virtual network is called a VPN. The (VPN) tunnel refers to network traffic that travels through a VPN, while all other traffic is referred to as outside of the tunnel.
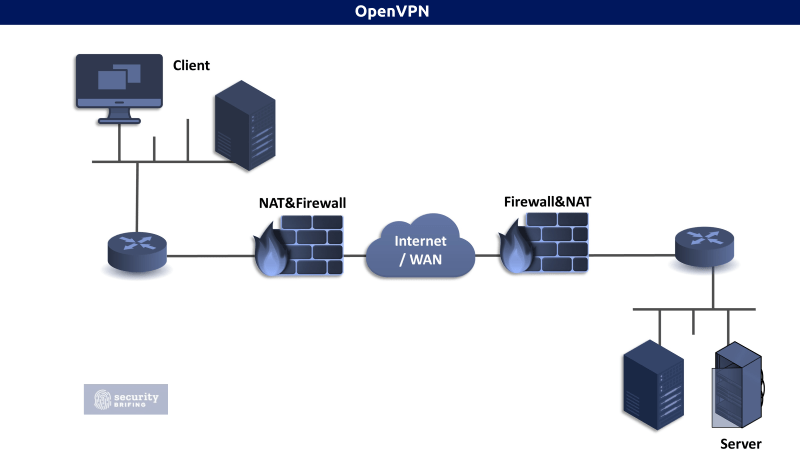
The following graph shows how network traffic travels through several sections of a network and the internet. Because HTTPS and SSH are more secure communications protocols, analyzing this sort of data is much easier. Someone must attack the network traffic in order to determine what type of connection is being established from which computer to which server, even if they can be seen.
When a VPN is used, the traffic inside the tunnel is no longer identifiable.
Which traffic can be routed through a VPN?
The virtual private network (VPN) can encrypt and tunnel any type of traffic, including pictures, movies, web surfing, emailing, and texting. Some popular programs that use VPNs are:
ATM Machines: By using a VPN, ATMs can connect to banking systems with increased security.
Public Wi-Fi: Public Wi-Fi networks are potential hotbeds for security attacks. By using a VPN, you can encrypt your traffic so that no one can snoop on your data.
Home Networks: You can use a VPN to connect to your home network anywhere. This is especially useful if you have a smart home with devices that need to be connected to your home networks, such as a security camera or a home automation system.
Bypassing Country Censorship: For people living in oppressive regimes, such as North Korea or China, censorship from government blockades is a pressing concern. The “Great Firewall of China” stops citizens from accessing the outside world and getting news and information that could inspire rebellion—VPNs provide a way to get around these restrictions.
Business Networks: Corporations and other organizations may use a VPN to connect multiple office locations or even entire data centers. By doing so, they can improve communication and collaboration between employees while also safeguarding sensitive data.
GeoIP Services: Several websites, including Hulu, YouTube, and Netflix, use GeoIP databases and other records to deliver content based on location. You can access material unavailable in your area by “bouncing” your computer connection through a VPN server closer to the desired geographic region. Additionally, a VPN will protect you from any legal penalties associated with watching banned films or copyrighted TV programs.
The private tunnel is entirely sealed off from the public internet. Although the VPN itself travels across the internet like in the picture above, devices along its route will only be able to see VPN traffic; they won’t know what’s being transmitted inside the secure tunnel. That’s because a VPN not only encrypts traffic within it but also individual data streams from other users outside it. In other words, even if someone was able to intercept one of these data streams, they wouldn’t be able to decode it because the VPN would still encrypt it.
The routers and firewalls on both sides create the tunnel. If you don’t take special measures to control VPN traffic, all network traffic passing through the VPN tunnel will omit any usual security measures.
Data encryption and authentication
VPNs use encryption and authentication to keep other people from seeing your data. Encryption makes the data hard to understand, and authentication ensures that only the right people can see it.
The first layer of security is authentication, which verifies that only authorized users can access the service. This might be done with certificates for each user or a username and password. After that, users may establish their own restrictions, such as certain routes or firewall settings. These are generally confined to one installation; however, they can be customized.
Secondly, we need to protect the communication channel more. To do this, we will sign each packet that is transmitted. This means that each system will verify that the VPN packets it receives are properly signed. By authenticating packets that have been encrypted, a system can save processing time by not decrypting packets that don’t meet the authentication criteria. If we keep the signing keys safe, this prevents denial-of-service attacks!
PPTP vs OpenVPN
Developed by Microsoft, the PPTP (Point-to-Point Tunneling Protocol) is one of the oldest and most common VPN protocols. OpenVPN is a bit more modern and can be more secure if configured correctly.
OpenVPN uses SSL/TLS for encryption, the same technology your web browser uses to connect to secure websites. OpenVPN is more flexible and can be configured for different use cases, while PPTP is very easy to set up but less flexible.
Although OpenVPN is more secure than PPTP, it can be more difficult to set up. If you’re not comfortable configuring a VPN, you may want to use PPTP.
How to use OpenVPN?
For Windows platforms
First, you need to download the OpenVPN client. Windows and Mac users can find the latest version, V3, here.
After you’ve installed the OpenVPN client, launch it and import the .ovpn file from the
Once you have installed the OpenVPN client, you must download a configuration file. This file tells the OpenVPN client how to connect to the VPN server. You can get this file from your VPN provider.
Once you have downloaded the configuration file, open it with the OpenVPN client. The OpenVPN client will ask you for your username and password. After you have entered these, the OpenVPN client will connect to the VPN server.
OpenVPN is now running in the background. You can verify this by checking your IP address. To do this, visit whatismyip.com. You should see that your IP address has changed.
For macOS platforms
If you are using a Mac, you can use the OpenVPN client for macOS. The latest version can be downloaded here.
Once you have installed the OpenVPN client, you must download a configuration file. This file tells the OpenVPN client how to connect to the VPN server. You can get this file from your VPN provider.
After downloading the configuration file, open it with the OpenVPN client. The OpenVPN client will ask you for your username and password. After you have entered these, the OpenVPN client will connect to the VPN server.
OpenVPN is now running in the background. You can verify this by checking your IP address. To do this, visit whatismyip.com. You should see that your IP address has changed.
For Linux platforms
If you are using Linux, you can use the OpenVPN client for Linux. The latest version can be downloaded here.
Installation for Debian and Ubuntu
If you are using Debian or Ubuntu, you can install OpenVPN with the following command:
- Open the Terminal by pressing ctrl + alt + T
- Enter the following command into the Terminal:
sudo apt install apt-transport-https. Then Enter the root password. - Type in the following command:
sudo wget https://swupdate.openvpn.net/repos/openvpn-repo-pkg-key.pub. This will download the OpenVPN repository key used by the OpenVPN 3 Linux packages. - Enter the following command into the Terminal:
sudo apt-key add openvpn-repo-pkg-key.pub - Enter the following command into the Terminal:
sudo wget -O /etc/apt/sources.list.d/openvpn3.list https://swupdate.openvpn.net/community/openvpn3/repos/openvpn3-$DISTRO.list. Depending on your Debian/Ubuntu distribution, you need to replace $DISTRO with the correct release name from the table below. - Enter the following command into the Terminal:
sudo apt update - Enter the following command into the Terminal:
sudo apt install openvpn3. This code will install the OpenVPN 3 package.
Installation Using .ovpn Profile
If you have an OpenVPN profile (.ovpn file) from your VPN provider, you can use this profile to connect to the VPN server.
- To create a one-shot configuration profile, type the following command into Terminal:
openvpn3 session-start --config ${MY_CONFIGURATION_FILE}. - Type the following command into the Terminal to import a configuration file and start a VPN session:
openvpn3 config-import --config ${MY_CONFIGURATION_FILE}. - To establish a new VPN connection from an imported profile, use the following command:
openvpn3 session-start --config ${CONFIGURATION_PROFILE_NAME}.
Installation for Red Hat Enterprise Linux or Scientific Linux
If you are using Red Hat Enterprise Linux or Scientific Linux 7, you can install OpenVPN with the following command:
- Go to the search bar and type in “terminal.“
RHEL/CentOS 6:sudo yum install https://dl.fedoraproject.org/pub/epel/epel-release-latest-6.noarch.rpmRHEL/CentOS 7:
sudo yum install https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
On RHEL 7, it is also recommended to enable the optional, extras, and HA repositories since EPEL packages may depend on packages from these repositories:sudo subscription-manager repos --enable "rhel-*-optional-rpms" --enable "rhel-*-extras-rpms" --enable "rhel-ha-for-rhel-*-server-rpms"RHEL/CentOS 8:
sudo yum install https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpmEnable the required services on Red Hat 8.codeready-builder-for-rhel-8-${ARCH}-rpms repository since EPEL packages may depend on packages from it: sudo ARCH=$( /bin/arch ) followed by sudo subscription-manager repos --enable "codeready-builder-for-rhel-8-${ARCH}-rpms"Additionally, for CentOS 8 users it is recommended to enable the PowerTools repository as some EPEL packages may depend on additional packages from it:
sudo dnf config-manager --set-enabled PowerTools - Install the yum copr module first. To do this, run the following command:
sudo yum install yum-plugin-copr. - Turn on the OpenVPN 3 Copr repository with the Copr module activated. To do so, use the following command:
sudo yum copr enable dsommers/openvpn3 - After installation, the OpenVPN 3 Linux client can be launched using the following command:
sudo yum install openvpn3-client
OpenVPN is a powerful and flexible tool that can be used to secure your entire internet connection. It’s important to understand the basics of how VPNs work before you start using one, but once you do, OpenVPN can be a great way to keep your data secure.
César Daniel Barreto
César Daniel Barreto is an esteemed cybersecurity writer and expert, known for his in-depth knowledge and ability to simplify complex cyber security topics. With extensive experience in network security and data protection, he regularly contributes insightful articles and analysis on the latest cybersecurity trends, educating both professionals and the public.